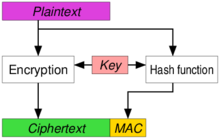
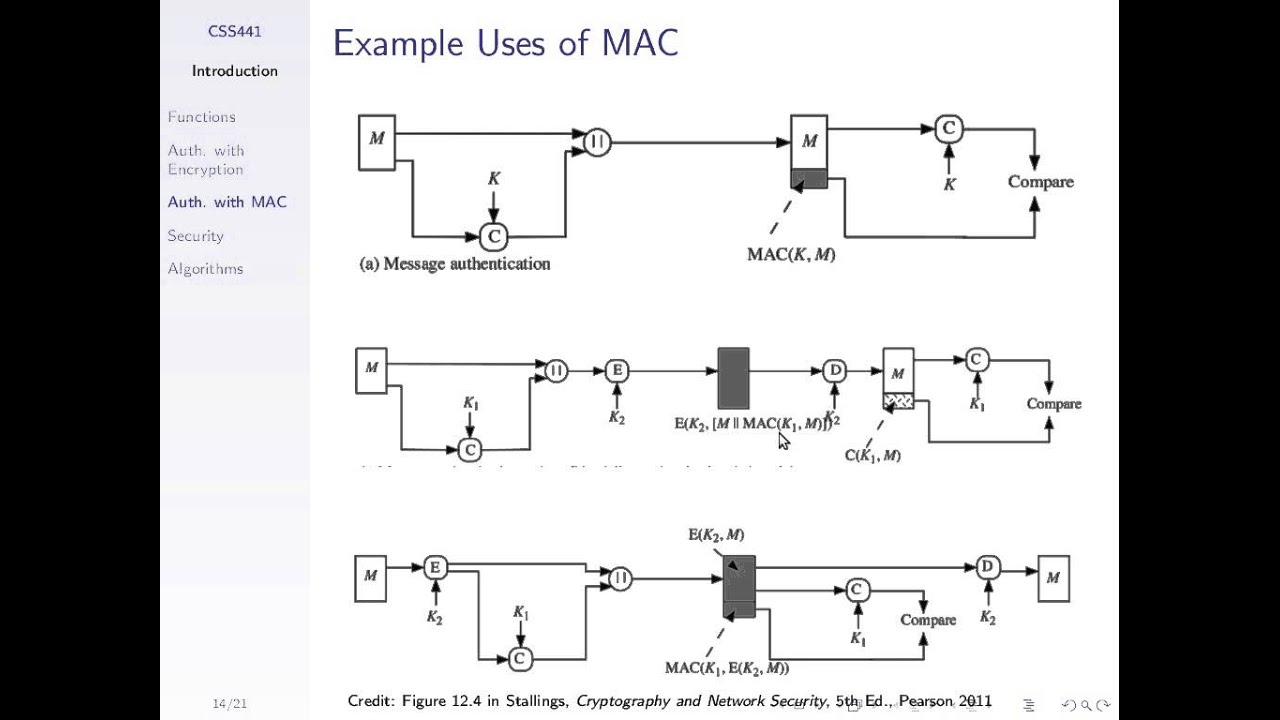
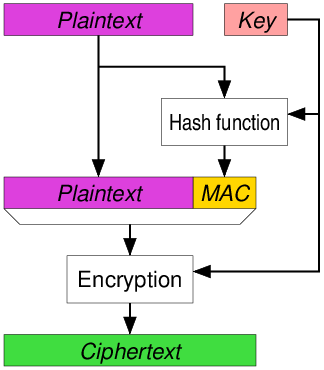
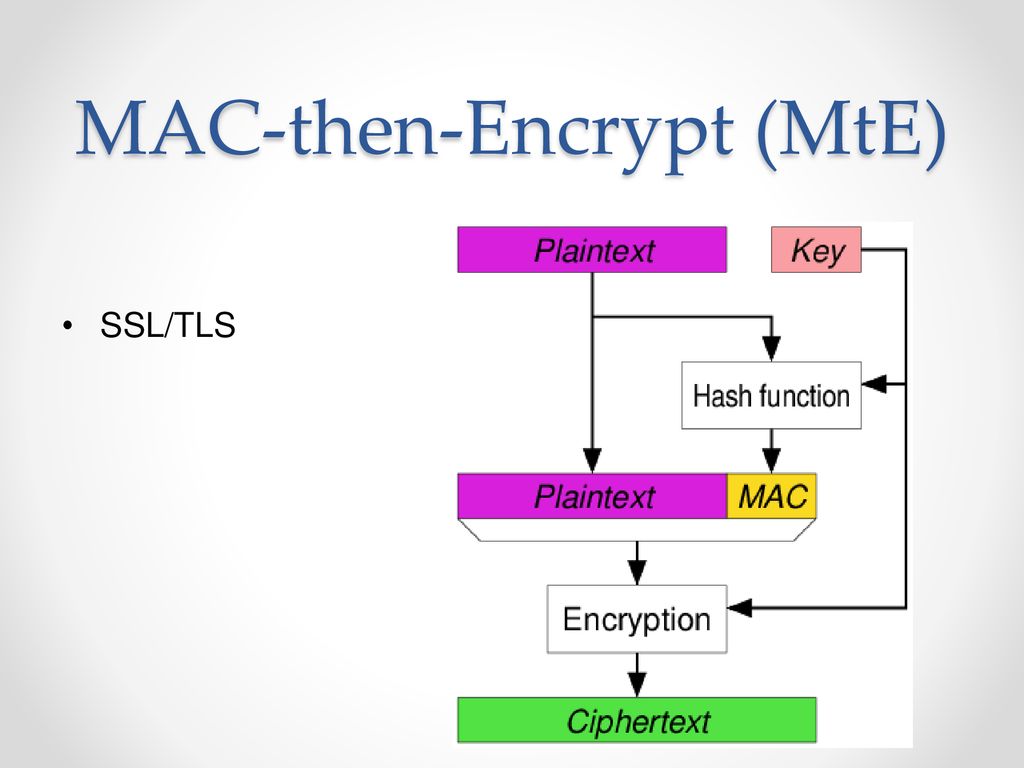
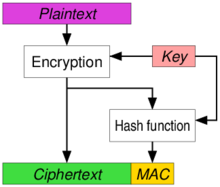
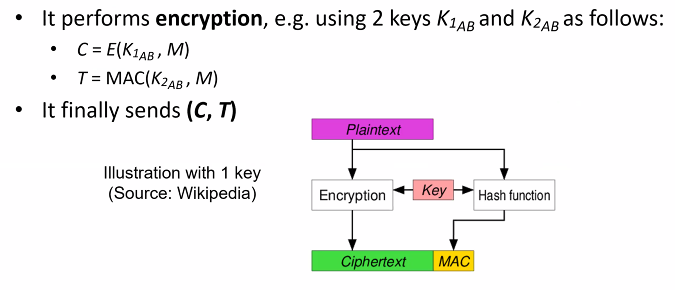
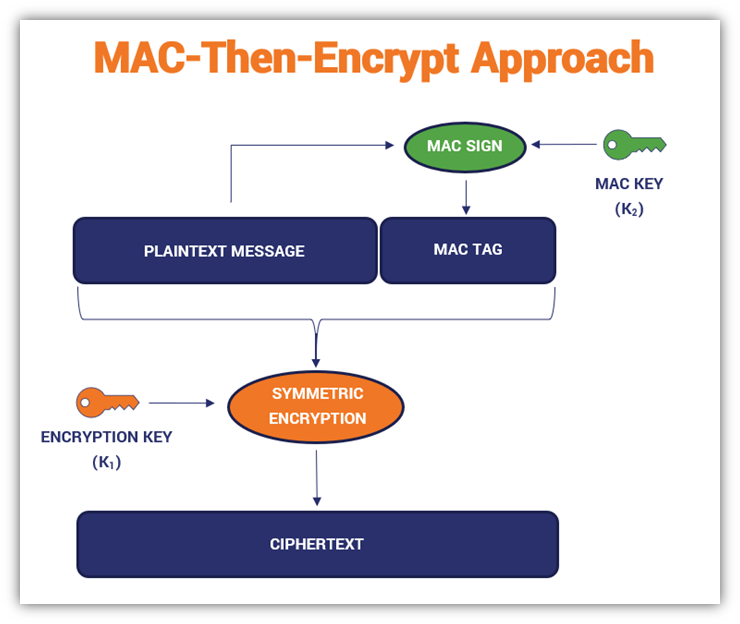
authenticated encryption - Why is a one-time MAC secure for MAC-then-encrypt with randomized-CTR but not randomized-CBC? - Cryptography Stack Exchange

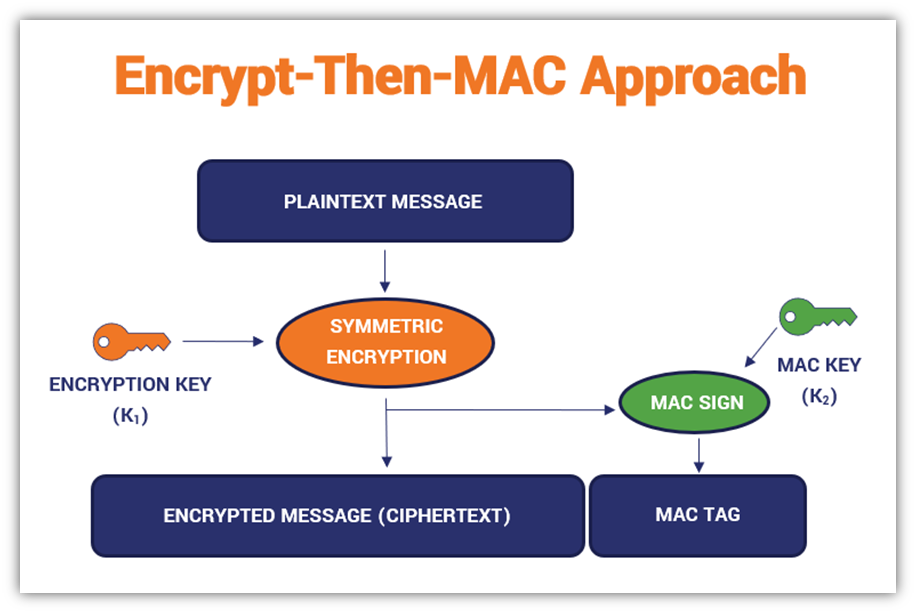
Architecture of the security module implementing the Encrypt-then-MAC... | Download Scientific Diagram
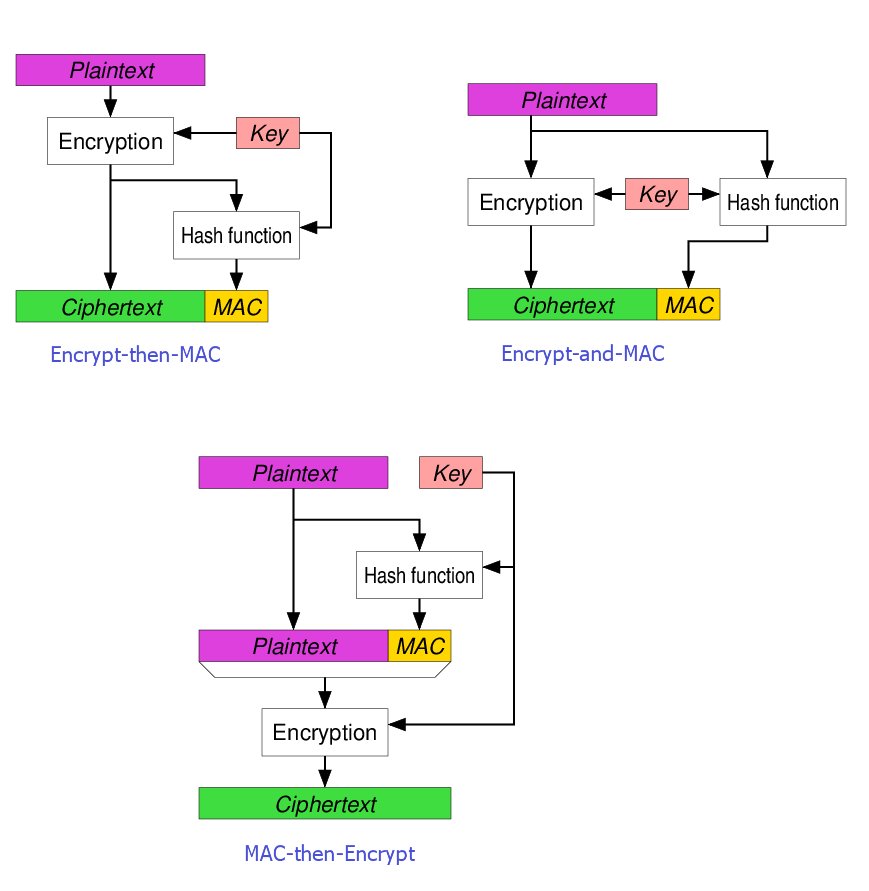
GK Palem on X: "Among the three methods for #Blockchain #Ciphers the Encrypt -Then-MAC has been regarded as the highest definition of security with "strongly unforgeable" MAC, compared with MAC-then-encrypt or Encrypt-and- MAC. Authenticated

hmac - Why do we encrypt then decrypt then encrypt data with different keys? - Cryptography Stack Exchange